I've been meaning to this for a while but never had time but now that I'm isolated I have all the time in the world.
Before I put out the steps I took to segregate my network I'll provide a list of the devices I am currently using and the software versions.
My network is driven by following devices:
- Unifi USG: Unifi USG
- Unifi 8 Port Switch 60W: Unifi 8 Port PoE Switch
- Unifi in-Wall AC access point: Unifi In-Wall
- Raspberry PI 4: Running unifi controller v5.12.66, PiHole v4.4 PiHole
I have several connected clients (devices) at any one time, most of which are IoT devices, because of security concerns I want to place all of these devices on a separate network where I'll apply firewall rules which will control the network access.
I currently have the following network setup:
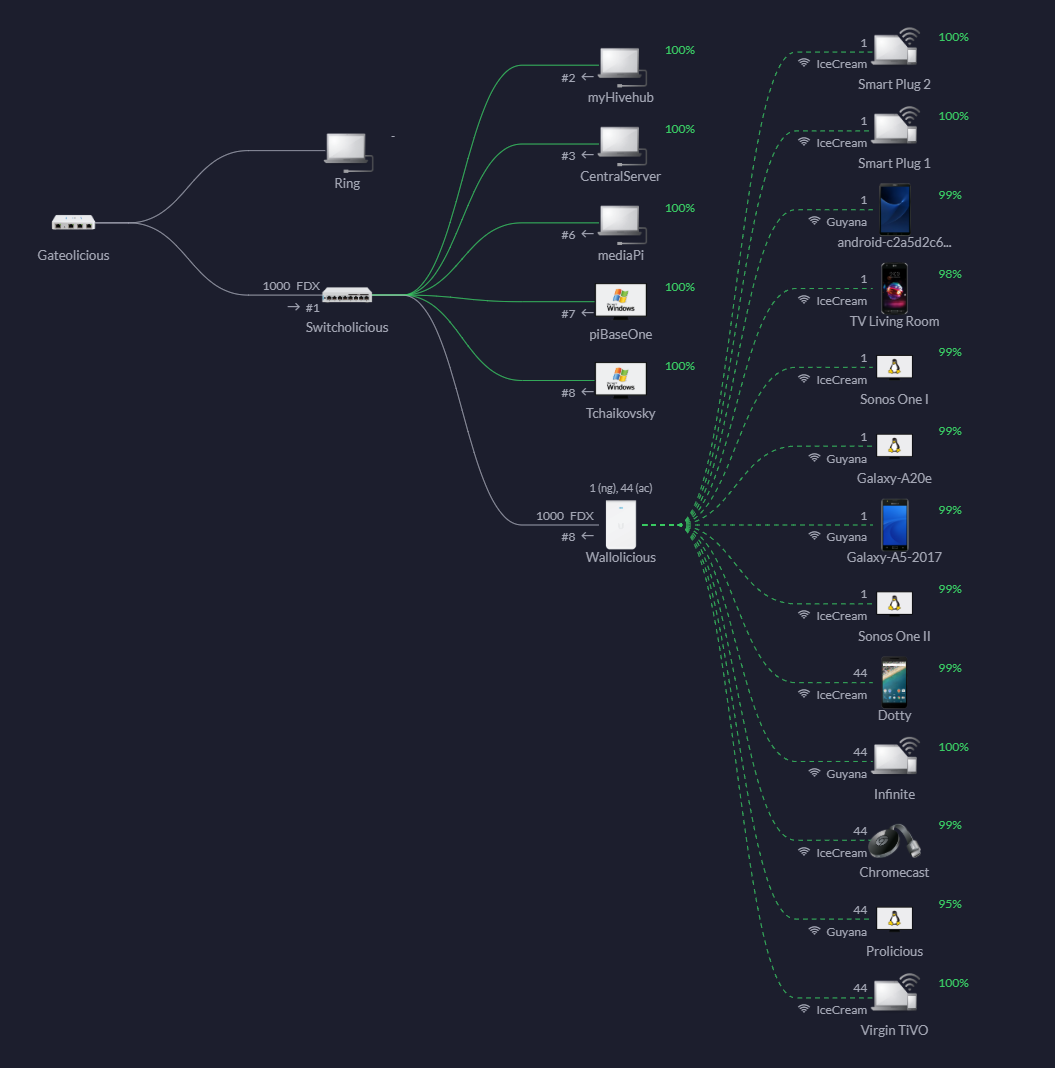
These instructions are specific to Unifi however the general principal should be applicable to other technologies. The main features that your network needs are: the ability to support virtual networks and the ability to configure firewall settings.
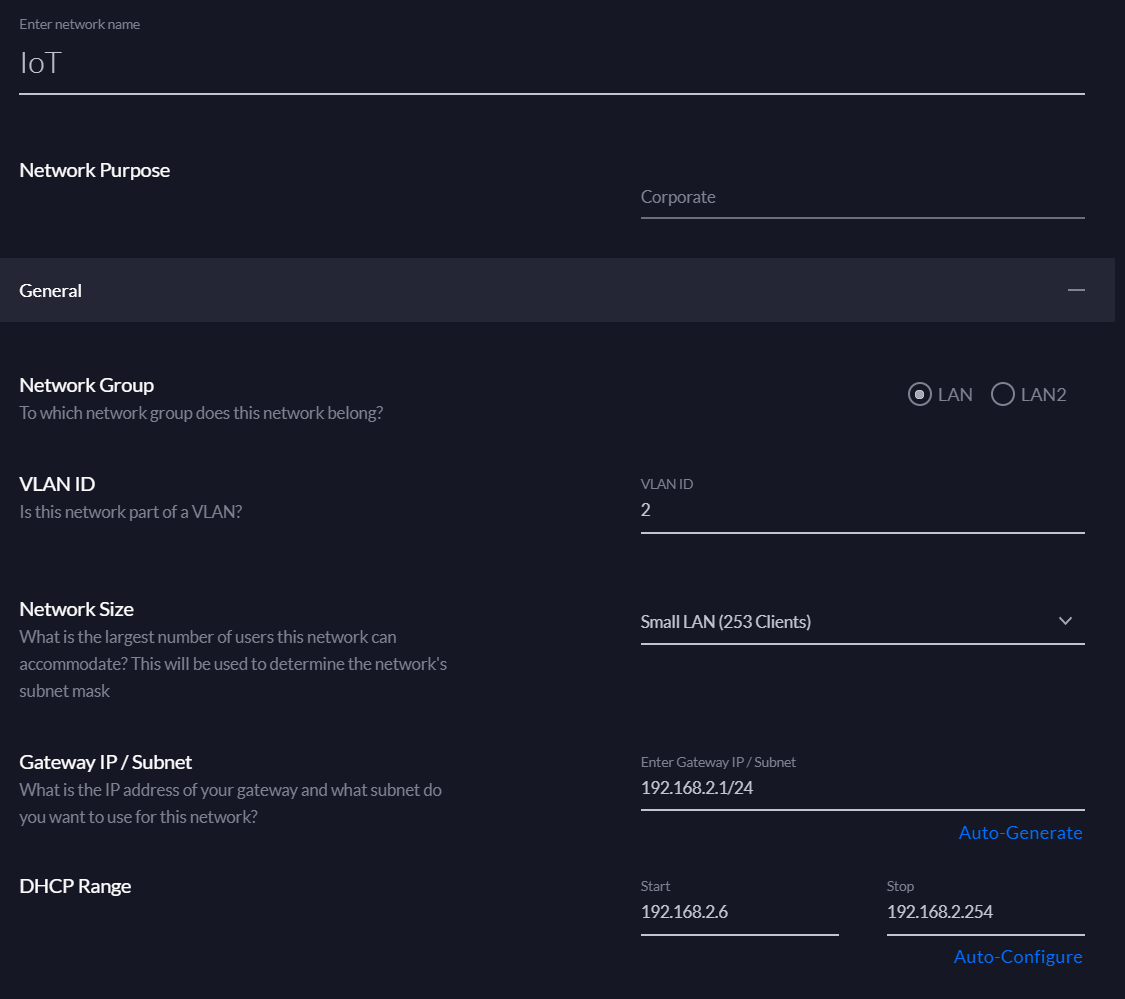
Firstly we'll need to create the network
- Go to Networks > Local Networks
- Give the network a meaningful name, I called mine IoT.
- Ensure that it's purpose (category) is set to Corporate.
- Specify a VLAN ID, I used 2. You just need to specific a numeric value that's not already in use.
- Specify a subnet/gateway CIDR address, e.g. I used 192.168.1.2/24. This allows for 254 IP addresses which is completely overkill but it works.
- For the DCHP range I specified the range: 192.168.1.6 - 192.168.1.254
- I have a Pi Hole DNS server on my network so I specify it's IP as the DNS server. If you don't have your own custom DNS server you can leave this value as automatic or set it to your current default.
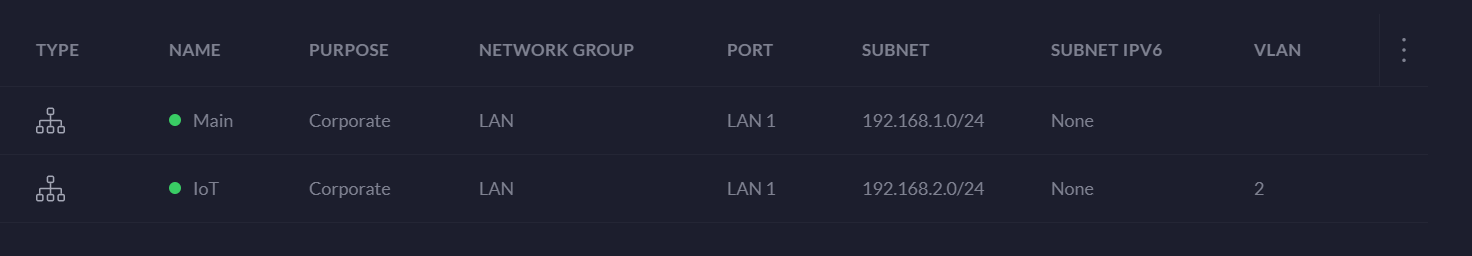
You should now have a minimum of two local networks
Once the network has been created I then went on to create the wireless network. This wireless network will be assigned an SSID which will be exclusively used for IoT devices.
- Go to wireless networks and create a new one.
- Set the SSID name.
- Set the level of security you require and set a security key (password).
- Select the use VLAN checkbox and use the ID value that you set on your IoT network.
- I left all of the other settings as their default.
- Now using a device (e.g. a smartphone) connect to the new wireless network.
- Check your local network IP address and ensure that it's in the range you specified above e.g. 192.168.1.2/24. You can also use the Wifiman app to check which devices you can see on your network.
Make sure you've established that you can connect to the internet on the new network because the following steps will affect what the new IoT network can do.
We are going to create 3 main rules which will prevent the IoT network from communicating with the main network, except to see the DNS server. The IoT network won't be restricted from accessing the public internet and the main network will have complete access to the IoT network.
- Open routing & firewall.
- Click on firewall then create new rule.
- Make sure that the rules are created on the LAN IN option. That is the local network going into Unifi's security gateway.
Firstly we will create some groups which will act as containers for some of the IPs and ports we want to apply our rules to.
Under Internet Security go to Firewall > Groups and create a new group, give it a meaningful name, e.g. LAN Group and add the following IPs:
- 192.168.0.0/16
- 172.16.0.0/12
- 10.0.0.0/8
Set the Type to IPv4 Address/Subnet. Save this group.
Create another group which contains the IP address of the DNS server, and create another group for the port of the DNS server, which is port 53. You should have three groups:
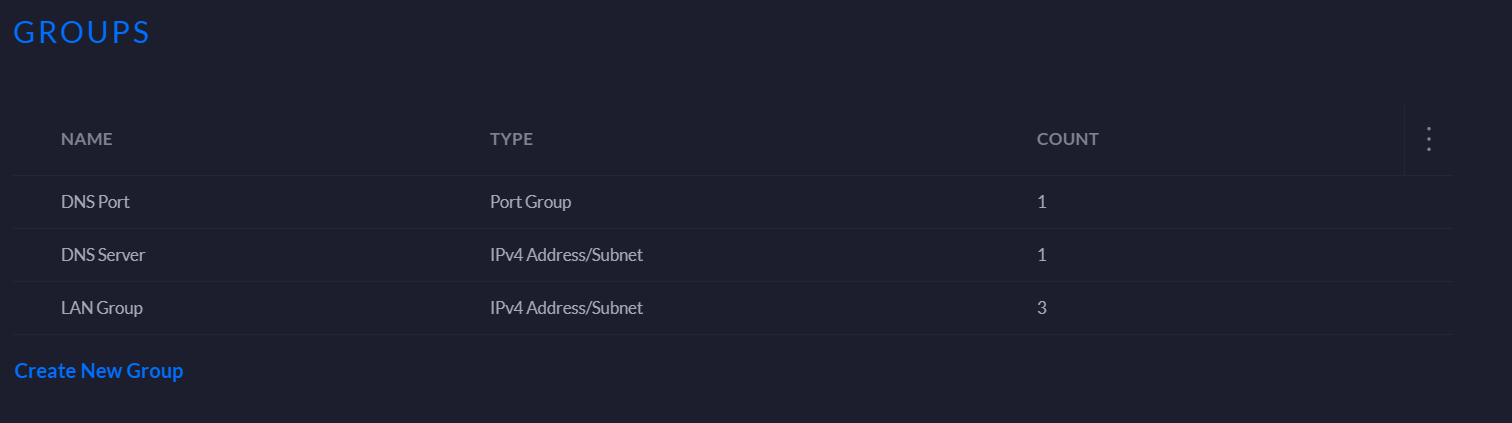
Next we'll create the firewall rules which will control traffic over the local network.
The first rule will allow all local network traffic into the IoT network. Now we'll create the first rule. Go to Internet Security > Firewall. Click Create New Rule and use the following settings:
- Set the Type to LAN In.
- Provide a meaningful description name, e.g ALLOW LAN to IoT.
- Set the Action to Accept.
- Set the IPv4 Protocol to ALL.
- Under Source, set Source Type to Address/Port Group.
- Set the IPv4 Address Group to ANY.
- Set Port Group to ANY.
- Under Destination set Destination Type to Address/Port Group.
- Set the IPv4 Address Group to ANY.
- Set Network Type to IPv4 Subnet.
- Click Apply. Then that rule is complete.
By selecting established and related this will ensure that no new connections can be made between the two networks. This prevents the IoT network from making any new connections to the LAN network and visa versa however the built in rule from Unifi on the LAN IN group will allow new connections between the two so we will need to create another rule to prevent those connections from the IoT network to the LAN network.
The next rule will allow traffic from the IoT network to communicate with the DNS server. Like a mentioned earlier I used the PiHole DNS sink server.
- Set the Type to LAN In.
- Provide a meaningful description name, e.g ALLOW IoT to DNS.
- Set the Action to Accept.
- Set the IPv4 Protocol to TCP and UDP.
- Under Source, set Source Type to Network.
- Set the Network to the IoT network IPs, e.g. IoT.
- Set Network Type to IPv4 Subnet.
- Under Destination set Destination Type to Address/Port Group.
- Set the IPv4 Address Group to address group created for the DNS server, e.g. DNS Server.
- Set the Port Group to port group created for the DNS port, e.g. DNS Port.
- Click Apply. Then that rule is complete.
The final rule will deny all traffic from the IoT network to the local network. Thus preventing the IoT devices from discovering or communicating with any of the devices on the local network.
- Set the Type to LAN In.
- Provide a meaningful description name, e.g DROP IoT to LAN.
- Set the Action to Drop.
- Set the IPv4 Protocol to ALL.
- Under Source, set Source Type to Network.
- Set the Network to the IoT network IPs, e.g. IoT.
- Set Network Type to IPv4 Subnet.
- Under Destination set Destination Type to Address/Port Group.
- Set the IPv4 Address Group to address group created for LAN, e.g. LAN Group.
- Set the Port Group to ANY.
- Click Apply. Then that rule is complete.
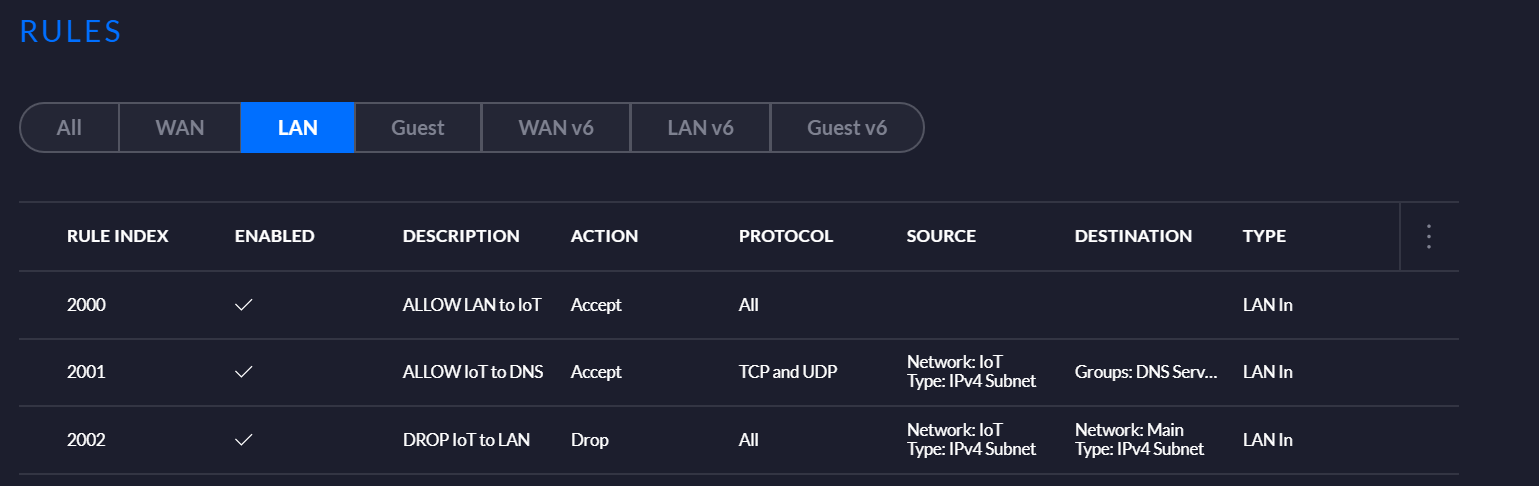
The above firewall rules should have been added in the LAN group.
After all of the rules were in place I then restarted my USG. This removes all of the known states for all of the current connections and forces new ones to be established.