OAuth 2.0 is a protocol (set of rules) which allows you to access a user's personal information without having to know their user credentials, i.e. username or password.
This is quite significant considering all of the issues surrounding security with user authentication, e.g. SSL, certificates, storage encryption etc.
What this means is you could access a person's Gmail account given just their permission.
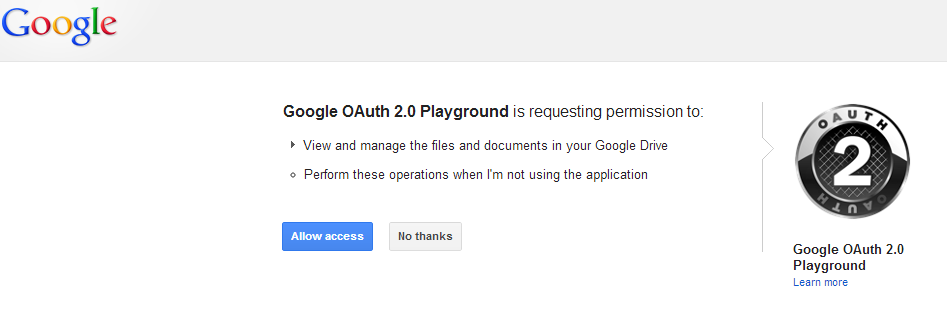
Screen shot taken from OAuth playground
How it works?
There are various processes involved in the OAuth 2.0 protocol, but the most common is the Authorisation Code Grant Flow.
The Authorisation Code Grant Flow allows a program to gain access to a user's personal information by access of a authorisation token.
The process works as follows:
- The program/application requests an authorisation token from their chosen provider along with what they want to access, e.g. the program might say, 'can i please have an authorisation token Google for Billy's Gmail account?'
- Billy then has to approved that request by simply saying 'yes' or 'no'.
- Assuming Billy said 'yes' then the program/application is issued with an authorisation token from the provider (Google).
- The program/application can then exchange this for an access token which is actually what is needed to access Billy's Gmail account. With that token the program/application can then read Billy's Gmail account.
The access token expires about every hour so the program/application will need to make sure that they request a new one!